Point-of-sale (POS) systems are at the heart of retail operations. They comprise everything from receipt printers to the software used to store and manage customer data. Regardless of whether a retailer operates a storefront or a large eCommerce operation, there is a POS system working behind the scenes.
As essential as POS systems are, they also present a prime opportunity for cyberattacks, especially with the evolution of sophisticated, automated cybercrimes that attackers have launched on POS environments.
It seems like the never-ending job of retailers to stay ahead of cyberthreats related to POS systems, but managing POS security can be an overwhelming job, especially when retailers rely on vast networks of devices, users, and vendors.
Data transmitted and stored by POS systems is especially attractive because of the wealth of personal and financial information that can be used and sold by cybercriminals. And it doesn’t take much to expose the information of millions of people.
Take the example of Wawa Stores POS system data breach from 2019 in which malware was detected on payment processing servers. While the company discovered the malware in December 2019, it had been active since March 2019–nine months of customer data potentially at-risk, including debit card numbers, cardholder names, and expiration dates. There isn’t evidence of unauthorized use, but it remains a disconcerting feeling for both customers and the retailer.
It’s difficult to permanently stop cyberthreats, but it is possible to enhance POS security with a few simple tips. Whether your company is a global retailer or an online store focused on eCommerce, you deserve to know that your network, users, and devices are completely secure using our handy POS security checklist.
What is POS Security?
When it comes to POS security, it’s important to understand what that pertains to. Many people are familiar with POS terminals and may not realize that there is an entire POS system beyond just a card reader and a cash register.
A POS system is made up of hardware, like receipt printers, card readers, touchscreens, and cash drawers, in addition to software. POS software is responsible for transmitting and storing data received during retail transactions. Without the software, POS terminals can’t properly function.
For POS systems, one of the greatest threats is malware. An attacker finds a vulnerability somewhere in the system and installs malware, giving them access to personal information and other data. Malware is a large umbrella that includes other malicious programs like adware, spyware, worms, and ransomware.
The increased reliance on eCommerce has also presented new threats, mainly in the form of web skimmers that gather personal information and data every time a customer makes a purchase.
One of the challenges with POS security is that there are so many components to POS systems. It’s tough to safeguard every attack surface completely, especially if an organization is using outdated operating systems, equipment, or insufficient remote access tools. This makes retail POS systems a prime target for cyberthreats and necessitates preventative action by retailers and their vendors.
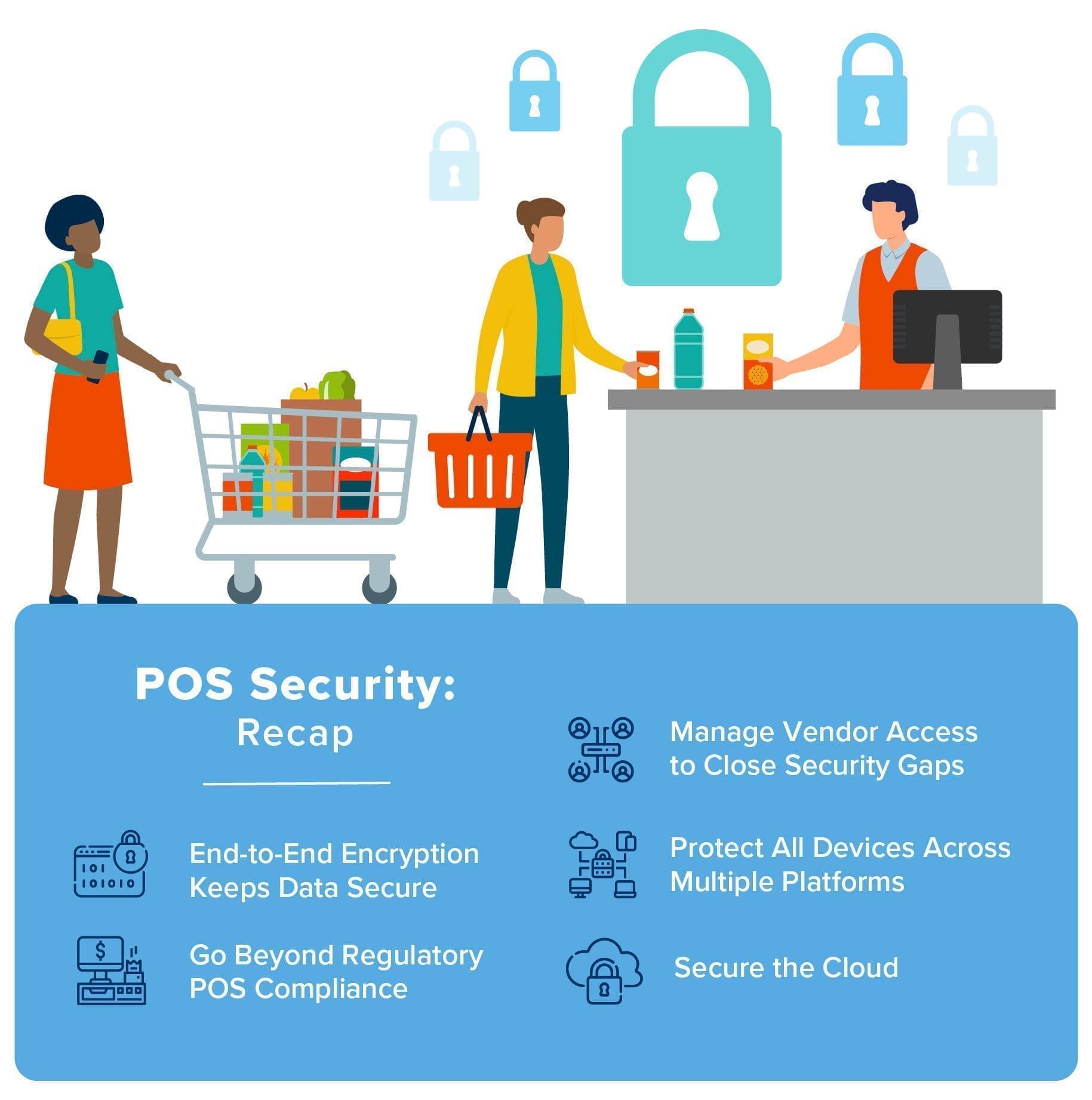
5 Point POS Security Checklist
The following POS security checklist offers a few of the primary ways to protect POS systems before a breach occurs:
1. End-to-End Encryption Keeps Data Secure
Encryption is an essential part of POS security, especially as it pertains to data being transmitted across a POS system. While many retailers and vendors may encrypt data, that doesn’t necessarily mean it’s encrypted from beginning to end.
End-to-end encryption means that data like credit card numbers and personal information are encrypted at every point in their lifecycle making it more difficult for attackers to access data. From the moment a customer swipes a credit card or enters personal information on a website, it is encrypted, or scrambled in such a way that only the receiver who has an encryption key is able to decode it.
Encryption is separated into two basic categories: data-in-transit and data-at-rest. Only protecting one leaves data at serious risk. Data-in-transit is information that is being moved from one location to another. For example, a POS terminal to a secure network. Data-at-rest is information that isn’t being moved and is currently inactive, but still vulnerable to attack.
Many regulatory bodies around the world require varying levels of encryption to protect data, with The California Consumer Privacy Act becoming the most recent to encourage stricter encryption. While it doesn’t explicitly state what encryption looks like, retailers and other types of organizations that store customer data are wise to implement strong encryption as a safety precaution.
So, what does the best encryption look like when it comes to POS security? Here are a few important aspects of comprehensive encryption:
- 256-bit encryption: Uses a 256-bit encryption key. There is also 128- and 192-bit encryptions. This means that an attacker requires 2256 combinations to break into an encrypted message, which is seen as nearly impossible. This level of encryption is best for data-in-transit that is moving sensitive information through a network.
- AES: A block cipher algorithm developed by The National Institute of Standards and Technology to help prevent brute-force (trial and error method) and other types of cyberattacks on government information.
- Easy to setup: Make sure any encryption tool or remote access software offers simple key management and implementation for IT teams.
- POS Compliance: Check regulations where the business is conducted to ensure that your POS security has proper levels of encryption. At a minimum, they should meet regulations, but for ultimate security, it helps to choose tools that exceed basic regulatory standards.
2. Go Beyond Regulatory POS Compliance


One example is the Payment Card Industry Data Security Standards (PCI DSS compliance). Any retailer conducting business with U.S. consumers must follow PCI DSS data security standards, which address everything from building and maintaining secure networks, to creating specific security policies. The goal is to protect credit card and personal data.
Other well-known and important regulatory bodies that affect retailers include GDPR (European Union) and the recent CCPA (applies to retailers conducting business in California).
Unfortunately for retailers, being compliant doesn’t equate total POS security. It’s a great foundation, but retailers still see cyberattacks even with the implementation of security practices.
A big reason for this is that retailers rely heavily on vendors and various forms of hardware and software to manage daily operations. With so many moving parts, it can be challenging to make sure that user access, authentication, and encryption is totally secure, especially as an organization grows and changes.
Outdated hardware and software used by a retailer or their vendors can be a major vulnerability, but with proper remote access software, those threats can be dramatically reduced. Check that remote access tools exceed basic regulations so that even as your business grows, you know you’re secure AND compliant.
3. Manage Vendor Access to Close Security Gaps
Partnering with vendors is an essential part of the retail industry, especially for larger organizations that operate globally. Vendors assist with everything from running IT support to managing electronic signage in stores. And they are all too often to blame for POS security breaches.
Why does this happen? In order for vendors to efficiently manage their operations, they require access to a retailer’s network. Ideally, they only have access to the specific parts of a network they need, but many times, they have access to places they do not need. This is where attackers find vulnerabilities.
A recent example is the breach of retailer Hanna Andersson’s POS system. In this case, their eCommerce platform vendor, Salesforce Commerce Cloud, was infected with malware that installed skimmers that collect customer information as it’s processed.
While many retailers may not be directly responsible for breaches like the one described above, they may incur penalties as a result, and may struggle to re-establish trust with customers following a breach. Vendors aren’t known by the public and thus, vendor attacks appear to be part of the retailer as a whole.
One of the best ways to prevent vendor vulnerabilities is with total control over user access. Granular controls over role-based access allow network administrators to define specific groups, users, and access levels so vendors can only get to where they need to be. This helps close the gap on potential entry points for malicious actors, whether they are hacking groups, or internal.
Retailers can also be sure to detail security protocols when creating service level agreements (SLAs) and ask vendors questions that pertain to POS compliance to make sure they are capable of managing POS security.
4. Protect All Devices Across Multiple Platforms
These days, retail transactions are happening in a variety of ways. Gone are the days of a basic POS terminal transaction, and welcome to the days of eCommerce and mobile usage.
Since so many customers are making purchases online and from their mobile devices, it becomes that much more important that POS security and remote access tools be completely secure. Statista found that as of December 2019, 40 percent of mobile device owners in the U.S. made a purchase using a mobile retail app. Customers are also using mobile wallets, which have their information stored on their device for quick and easy access, to make purchases.
The issue is that not all security tools have the ability to work across multiple platforms, operating systems, and devices, thus leaving them vulnerable. Choosing remote security tools that offer cross-platform compatibility and connectivity ensures that transactions and other actions are done safely. In addition to having these capabilities, it’s helpful to use one consolidated remote access solution versus many. The more solutions being used, the more costly, and the more vulnerable a system can be.
5. Secure the Cloud
Building off of the demand for eCommerce and mobile devices is the increasing use of the cloud. The cloud is basically a web-hosted POS system that retailers use when customers make online purchases. They can also be used to store data.


While the cloud is an efficient way for retailers to store and manage data, it also presents another way for attackers to test POS security, especially as retailers scale. Impero Connect is one remote access tool that offers comprehensive cloud security in the following ways:
- Deploys client, server, and gateway modules 100 percent on-premise
- Reduces interactions outside of LAN/WAN
- Easily scales with growing organizations
- Can be deployed in a single-tenant virtual private cloud
- Can be isolated by geography of retailer’s choice, or be a hybrid
Case Study: Toshiba 4690 POS System
Impero Connect is known for providing the most secure access to various devices, including the Toshiba 4690 POS system. This includes the TCx Sky operating system. What’s unique about Impero is that they help retailers and vendors remain compliant at scale. That means when your business expands, so does Impero’s secure remote access.
While Impero has worked to protect Toshiba 4690 systems, security is not limited to those devices. Impero’s secure remote access software allows other operating systems and networks connected to Toshiba 4690 to be compatible, maintaining total POS security. This works through Impero’s layer of centralized and consolidated software components:
- Guest: Workers remotely access and support any machine using a Host software and available on Windows, Linux, Mac, Android, iOS
- Host: Any target machine can be remotely supported by any computer running the Guest software
- Security server: offers centralized security management and logging for Windows only
Impero’s centralized location creates one place where role-based access, permissions, and logging options can be controlled, helping to streamline operations. Control over logging is particularly important in regard to POS compliance, allowing you to produce necessary logs for auditing purposes.
Secure Remote Access Tools for Secure Transactions
No matter what size retailer you are, where you operate, or if you have a brick-and-mortar storefront or an online shop, you need POS remote access that offers you total security and compliance in one tool. Impero Connect offers you and your vendors one POS security solution for accessing POS systems and protecting data at every level. In fact, 24 percent of the world’s largest retailers choose Impero for that very reason. Ready to try for yourself? Get a free trial of Impero Connect today!