Zero Trust Remote Access
Say goodbye to “trust but verify.”
Now it’s “never trust, always verify, enforce least privilege.” (Centrify)
What is the Zero Trust model?
Years ago, IT and security professionals began to give up on the concept of a security perimeter. It’s not feasible anymore to build a barrier around your corporate network and then assume all the activity on the inside is trustworthy.
Around that time in 2010 the Zero Trust security model was introduced by John Kindervag, a principal security analyst at Forrester Research. Zero Trust is about granting the least-privileged access necessary within an environment, based on 1) who is requesting access, 2) the context of the request, and 3) the risk of the environment being accessed.
“Zero Trust is a security concept centered on the belief that organizations should not automatically trust anything inside or outside its perimeters, and instead must verify anything and everything trying to connect before granting access.” CSO Magazine.
There are many benefits to taking a Zero Trust approach. In terms of risk reduction, it can help a company cut back on complexity, reduce its attack surface, and increase visibility for auditing and compliance.
When a business uses a VPN, it’s common practice to segment the network with VLANs and subnets, keeping the most sensitive assets and data in the most secure zones.
By contrast, Zero Trust architecture creates something closer to one-to-one segmentation. Moving laterally within the network is impossible, which prevents some types of attack entirely:
- DDoS attacks
- Server scanning
- Application exploits
- Man in the middle attacks
- SQL injection
6 Core Tenets of Zero Trust
Verify who: Make sure to integrate with directories rather than local accounts, because this keeps the number of vulnerable accounts and passwords to a minimum. Always use multi-factor authentication (MFA).
Contextualize requests: Before you approve any access request, be sure to understand the context. Then, once a request is approved, grant the minimum level of access necessary, and only for long enough to perform it.
Secure the admin environment: Try to keep access sources clean. If possible, ensure direct access can’t be made from workstations with open internet access and email (to avoid malware).
“The Zero Trust model of information security basically kicks to the curb the old castle-and-moat mentality that had organizations focused on defending their perimeters while assuming everything inside didn’t pose a threat and therefore was cleared for access.” CSO Magazine
Grant least privilege: Keep strong zoning in your network so there’s minimal ability to move laterally.
Audit everything: Audit logs are your friend in a Zero Trust framework, especially if you use a tool like Impero Connect that supports screen and video recording for sessions.
Adaptive control: Prepare to actively respond by ending sessions or following up with forensics when needed. In a Zero Trust model it’s important to get realtime notifications and closely monitor risky activity. For the sake of scalability, it’s important to keep controls flexible based on the risk context. Even if someone enters the proper credentials, you might want to require stronger verification, if a request is coming from a risky or unknown location or device.
“Zero Trust is multivariable in that it is dynamic and not static. It gives users one-time access to a requested application while all other resources are cloaked without granting access to the entire network.” Network World
Best Practices for Zero Trust Remote Access
Back in the day, an admin might only need to access data and resources on a private server, within a legacy system.
These days privileged access management (PAM) is a lot more complex.
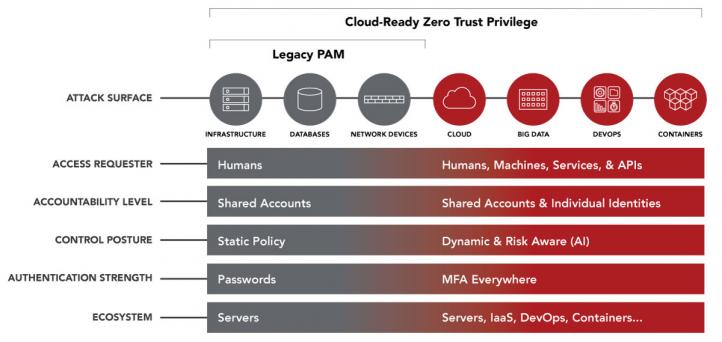
(Source: Centrify)
Admins and users need varying levels of access across cloud infrastructure, databases and network devices — not to mention containers, microservices, digital twins and more — seamlessly.
When you’re configuring remote access rules within a Zero Trust framework, there are a few best practices to follow:
Verify who: Make sure to enable strict authentication rules within a secure tool such as Impero Connect, including multi-factor authentication across the board.
Contextualize requests and grant least privilege: With an advanced tool, you can restrict authorization based on user groups, location, and IP address. With Impero Connect you can even grant access to specific whitelisted applications, or give time-based access. You can also apply function-based restrictions to a user or group, so they can only perform certain functions on specific devices or servers.
Auditing: Whereas VPNs don’t usually have built-in audit logging, remote access software like Impero Connect offers unalterable audit logs and full session recording — including video recording.
Conclusion
You can’t implement a Zero Trust framework without a secure tool for remote access. Try Impero Connect for 14 days.


