
Remote desktop hacks become a common way for hackers to access valuable password and system information on networks that rely on RDP to function. Malicious actors are constantly developing more and more creative ways to access private data and secure information that they can use as leverage for ransom payments.
It’s important that your company does everything possible to keep your network and system secure and protected from hackers. RDP is a common solution for businesses, but its ubiquity is precisely what makes it so vulnerable to an RDP hack. If you already employ Microsoft’s RDP as a remote desktop or remote support solution, it’s vital that you understand the risks and alternatives.
What is RDP?
If you are worried about an RDP hack, it’s important to know what RDP is and whether or not your company is already using it. RDP stands for Remote Desktop Protocol and is a remote desktop solution that comes pre-installed on all Windows PCs.
Companies that range in size from a handful of employees to thousands all use RDP regularly – and often for day-to-day activities. Since Windows computers are the preferred devices in most industries, RDP is a commonly used tool for many businesses.
Whether companies are using RDP to provide remote support or share files and data remotely, Microsoft’s RDP is the remote desktop solution of choice for many precisely due to the fact that it comes already installed. As a Microsoft-only product, RDP does present some limitations if people and employees in your network are using Mac, iOS, or Linux devices (if you’re looking for broader compatibility, check out Netop’s RDP alternative). But, the bigger issue with RDP is due to how common it is.
How Does an RDP Hack Happen?
RDP has become a common way for hackers to steal valuable information from devices and networks. It is specifically vulnerable because of its ubiquity. Since so many businesses use it, the odds accessing an improperly secured network are higher and hackers have a better chance of breaking through.
Additionally, the software on many networks is not up to date. Out of date versions of RDP without the latest security patches are even more vulnerable to attacks. Once Microsoft discovers a vulnerability in its RDP it releases an update to fix it. But it’s on the system administrator to ensure that every device is updated in order for the patch to take effect. Hackers can successfully employ an old RDP hack on devices and networks that are out of date.
The scariest part about an RDP hack is this: if your uses Windows computers and RDP for remote desktop or remote support purposes, you are vulnerable to an RDP hack.
What is RDP Hacking?

Hackers use various techniques to break into vulnerable networks, servers and devices via RDP. RDP hacking has become so common that there are even articles published publicly to the internet with instructions on how to employ an RDP hack.
In this how-to article, hackers walk through the various steps you take to steal a “sysadmin” (system administrator) password through vulnerable RDP connections. While it requires some fundamental computer administration skills to accomplish, RDP hacking is easy and common enough that almost anyone can learn how to do it.
Once a hacker has access to the sysadmin password, they have full access to the network and devices within it. One of the most common ways that malicious actors use this access is to leverage it for a reward payment – this is known as “ransomware.”
Hackers use RDP to gain access to the host computer or network and then install ransomware on the system. Once installed, regular users lose access to their devices, data, and the larger network until payment is made. It’s a situation no business or organization wants to find itself in – which is why it’s so important to adequately protect yourself and your company against an RDP hack!
Remote Desktop Hacks and the Dark Web
Did you know that there are entire websites on the dark web devoted to illegally selling access to RDP servers? Besides a ransomware attack, another common outcome from an RDP hack is that hackers will sell your RDP system information on the dark web.
Though you need access to a dark web browser like Tor to view them, there are several sites on the dark web that sell access to servers, networks, and devices that were obtained through RDP hacking.
According to Bank Info Security, access to hacked RDP servers sold for anywhere from $3 to $15 in 2017. While this might seem like a small amount of money, RDP info is likely being purchased on a large scale. Hackers employ their attack on as many different RDP servers as possible then sell the stolen info in bulk.
One of the scarier things about any malicious attack is that you might not be aware that your system has even been compromised until the security information is sold to a third party who then decides to leverage it against you.
Components of Secure Remote Access
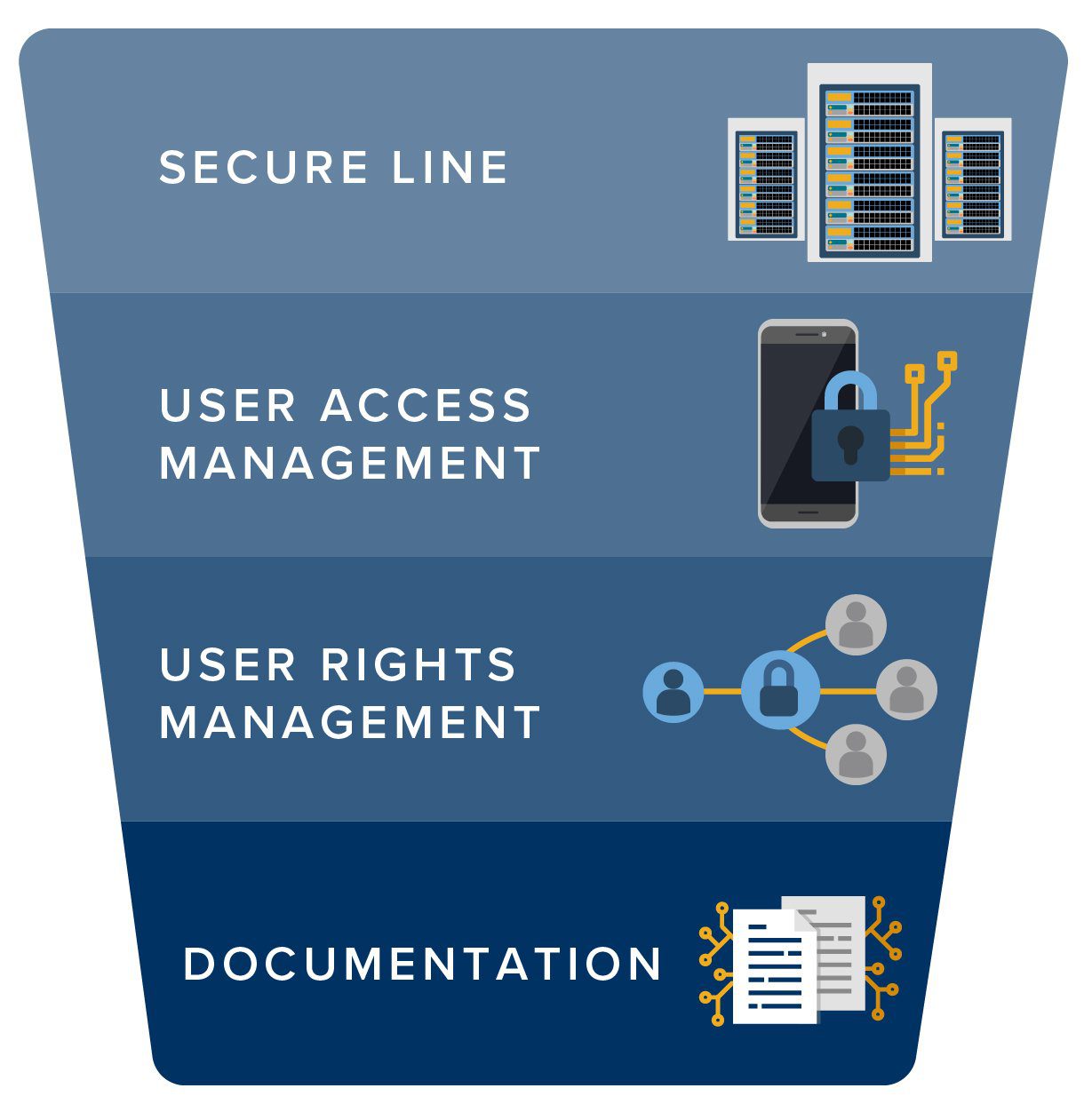
Remote desktop hacking is scary – but there are precautions you can take to protect your company and your data. Netop offers secure remote support software that was built around protecting your data.
With all of the same benefits and features of RDP, Netop’s remote desktop and support solution can help your business run more efficiently without opening your network up to an RDP hack. Netop’s industry-leading security features are based on a multi-layer approach:
- The first layer is a secure line, which simply means that Netop’s remote access is managed through your company’s own servers – ensuring that corporate security policies aren’t compromised.
- The second layer is user access management – this makes sure that target devices have specific criteria for accepting incoming invitations to connect.
- The third layer is user rights management, which allows different users to have different access profiles, enabling companies to define user rights down to the smallest criteria.
- The fourth security layer is documentation – Netop keeps track of all activity, providing you with the most thorough audit trails available.
The facts are clear: if you’re using Microsoft’s RDP for your remote support and/or remote desktop needs, your system, network, devices, and data are all vulnerable to a remote desktop hack. The best way to protect yourself and your company from an RDP hack is to switch to a more secure alternative remote desktop software.
Sign up for a custom demo of Netop Remote Control and see the security capabilities for yourself.


