

The goal of the Payment Card Industry Data Security Standard (PCI DSS) is to provide regulatory guidelines that secure customer data and enhance global security, which ultimately helps merchants succeed in their businesses.
Yet, for many organizations, it can be confusing to know if they’re fully compliant and frustrating to keep up with changing standards, especially when they’re partnering with vendors to manage operations.
One way to approach PCI DSS compliance is to better understand PCI scoping and how to define different aspects of your data environment. With the proper information about what scoping is and how to define a PCI scope, retail organizations can reduce compliance and operations costs, and avoid the potential penalties.
What Does PCI Scope Mean?
Scoping as defined by the PCI DSS requirements identifies the “people, processes, and technologies that interact with or could otherwise impact the security of CHD [cardholder data].” Essentially, any components of a system related to CHD that fall under PCI DSS. These components include the flow of cardholder data environment (CDE), and any other components that are connected to the system or support it.
Within PCI scoping there are three distinct ways that CHD is managed:
- How it’s stored
- How it’s processed
- How it’s transmitted
To accurately access and define a PCI DSS scope, organizations need to create a data flow map to assess how CHD moves through a system. This helps organizations see which parts of that system need proper security in addition to remaining compliant. Examples of components are those that make a network connection to a system are:
- Hardware: Personal computer, POS terminal, mobile devices and any other hardware that is used to process data
- Software: Payment processing software
- Networks: Ethernet, Bluetooth, firewalls, or any virtual connection used to communicate between various parts of a system
Why is PCI DSS Scoping Important?


With accurate scoping, organizations can:
- Pinpoint the exact places that need PCI controls, and where they don’t
- Provide better security and compliance
- Avoid unnecessary costs of using additional security controls that aren’t needed
The process of identifying what falls under PCI scope also helps organizations identify those areas that aren’t in scope, known as “descoping.” The process of descoping allows organizations to minimize the security controls needed to protect the CDE. Descoping can involve the following:
- Limiting how many people have access to the system (user access)
- Simplifying processes
- Identifying the technology and software that best serves the unique CDE
So, how can your organization reduce PCI scope to be more efficient and secure? The following sections will offer tips to help you descope relative to your CDE and build a stronger system.
How to Reduce PCI DSS Scope
There are a number of effective strategies to reduce PCI scope which involves limiting access to CHD and where it’s transmitted. A combination of the following strategies, which are offered with secure remote access tools, can be an effective way to enhance your security and ensure total compliance.
1. Reduce CHD Interaction with Network Segmentation

A few examples of network segmentation are:
- Installing a network firewall between CDE and network
- Installing and updating anti-virus software to protect against malware
- Enforcing strong passwords at every level for all users including vendors
An example of network segmentation in practice is separating a medical device from a specific network to prevent devices from being affected by visitor web browsing.
Benefits of network segmentation include:
- Limiting damage from a cyberattack: if there is an attack, segmentation can prevent that malware from moving to other parts of your system.
- Protects devices: Some devices are more vulnerable and thus need more protection from cyberattacks that may come through Internet usage.
- Limits the number of PCI scoped systems: compliance requirement and auditing only applies to the systems in-scope, which can save money and time.
2. Point-to-Point Encryption to Protect Data


Encrypting with strong cryptography is an acceptable way to meet PCI DSS requirement 3.4 but may not be enough to keep CHD fully out of scope. Since an organization (on-premise) has the encryption keys stores in their system, it technically means that CHD is accessible if a cybercriminal was able to hack into the system. If a vendor holds the encryption keys, it may reduce PCI DSS scope.
For on-premise encryption to reduce scope and remain compliant, an organization has to use point-to-point encryption (P2PE). This involves securing data from the moment it’s captured to its endpoint where it will be stored. This secures all CHD data that goes into hardware like a PIN pad, or other POS devices. Using P2P encryption, even on devices that are out of PCI scope provides the most security.
Benefits of P2PE for your system include:
- Reduces risk of losing CHD since it’s impossible for data to be decrypted in your system
- May reduce PCI DSS scope
- Make PCI DSS compliance simpler due to fewer requirements
3. Keep Data Moving Safely with Tokenization
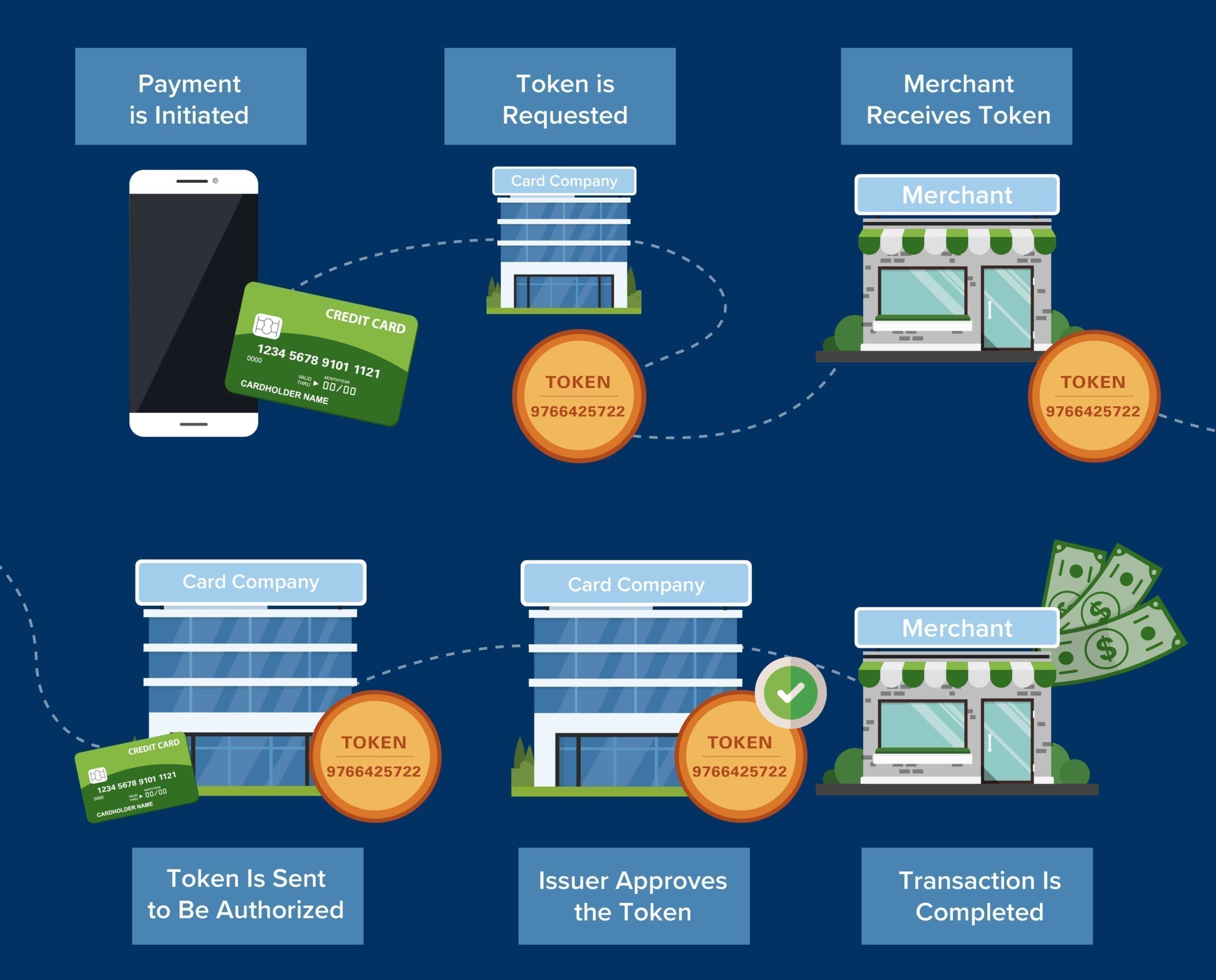

To properly secure this data, tokenization should happen outside of your system so that it never touches any aspect of your environment. This allows organizations to remove their networks from PCI scope and remain compliant. The sooner tokenization happens in the CHD journey, the more likely you are to reduce scope.
Benefits of tokenization include:
- More secure environment with fewer data breaches
- Compatible with different types of payments
- Works on personal information in addition to credit card data
4. Outsourcing to Avoid PCI Exposure


One example of this is POS remote access. A compliant, effective remote access tool allows you to consolidate security solutions for devices and networks with one tool to provide high-quality protection from data breaches and threats to CHD. Some of the benefits of using compliant secure remote access are:
- End-to-end encryption
- Complete auditing logs
- Multi-factor authentication
- User access controls
While this may help reduce scope, it may not eliminate it. Additionally, it’s important to check that any vendor you are considering can provide evidence of their PCI compliance. Partnering with vendors can be costly, but it may also reduce costs related to PCI scope and be more secure than your own environment. If you’re saving money from reducing PCI compliance, the cost of a vendor may be worthwhile.
Myths About Reducing PCI Scoping
As you consider PCI compliance for your organization and reducing PCI scope, there are a few myths to be cautious of before choosing products and services. This can be especially important for smaller organizations that may be overwhelmed by the numerous options available and the overwhelming about of PCI requirements. The following are a few common myths:
Myth 1: A Single Vendor Can Make an Organization Compliant
There are 12 PCI DSS requirements for organizations to meet, but there are not many vendors that can meet all 12. They address certain aspects of your system and PCI compliance, and can be viable solutions for reducing certain parts of PCI scope, but you still have to look at security for your whole system.
Merchants and vendors need to find compliant tools to address each of the 12 requirements rather than one catch-all answer to PCI compliance.
Myth 2: PCI Compliance Ensures Security
Cybersecurity and protecting CHD goes beyond PCI compliance. While it is certainly an important part of your security protocols, cybercriminals are continually finding new ways to access systems and PCI standards have to change to adjust. One successful completion of PCI assessment doesn’t ensure compliance or safety moving forward.
One way to support your system as standards change is to choose tools that exceed compliance. Whether it’s remote access software, hardware, or IT services, the only way to ensure compliance is to make sure your partners are capable of addressing changes to PCI standards.
Myth 3: We Have to Store CHD in Our System
It’s suggested by PCI DSS and payment card companies to NOT store CHD if you’re a merchant. You’re actually not permitted to store data from the magnetic strip on cards and any information from the front of the card has to be encrypted per PCI DSS standards.
Myth 4: Completing a Self-Assessment Questionnaire (SAQ) Makes us Compliant
Some merchants aren’t required to have on-site assessments to confirm PCI compliance, so an SAQ can satisfy PCI scope at that time. But as standards change and you rely on different tools and services, your system will require continuous passements to ensure compliance and total security.
Choose Impero Connect to Remain PCI DSS Compliant
Remaining PCI compliant essential for your organization’s security and to avoid potentially large fines. A 2018 Cost of a Data Breach Study from the Ponemon Institute found that the average cost of a data breach around the world was $3.86 million, which was up from the previous year. With that kind of trajectory, one may expect that fines could continue to rise as PCI standards updates occur.
Staying on top of changing standards, whether for PCI scoping or other regulatory bodies, is not only a legal matter, but a security one. If you need a secure remote access solution, look no further than Impero Connect. With our software, you can rest assured that your devices, platforms, and networks are secure no matter where you’re connecting from. Contact us today for a free trial to learn how we can support you in remaining PCI compliant.




