
How often have you heard about data breaches related to retailers in the past few years? From the more notable incidents, like the massive Target breach in 2013, to recent issues announced by Macy’s and Marriot, it’s increasingly clear that retailers are a prime target for attackers using POS malware to skim for sensitive information.
While the media often covers the data breaches that affect larger retailers, small to medium-sized businesses are just as much, if not more vulnerable to POS cyberattacks because they often do not implement proper security measures. Unfortunately, attackers are aware of this leading to a costly, time-consuming recovery process.
Why are POS systems so vulnerable? Many POS systems run off of unsecured or outdated operating systems. Information from the POS device is moved and stored, sometimes without proper encryption, where it may be vulnerable to malware. Additionally, if that same device, network, or operating system is accessed by multiple users, security gaps increase.
Fortunately, there are effective retail remote support solutions that offer tools to help businesses prevent and identify attacks. To better understand the need for these tools, we’ll first take a look at the primary concerns related to retail cybersecurity.
Whitelisting is Not Properly Applied to POS Systems
If you work in the world of IT you are familiar with both blacklisting and whitelisting. Traditionally, blacklisting is a common security practice, which denies access to known malicious entities. This can be effective and useful when systems need to be accessed by many users.
Problems arise, though, when systems contain sensitive information that should only be accessible to select users. This is where whitelisting can be an effective practice. Whitelisting grants access based on pre-defined protocols such as approved users, IP addresses, and applications. Blacklisting defines access by what entities shouldn’t be doing; whitelisting defines access by what entities should be doing.
How Whitelisting Helps Retailers
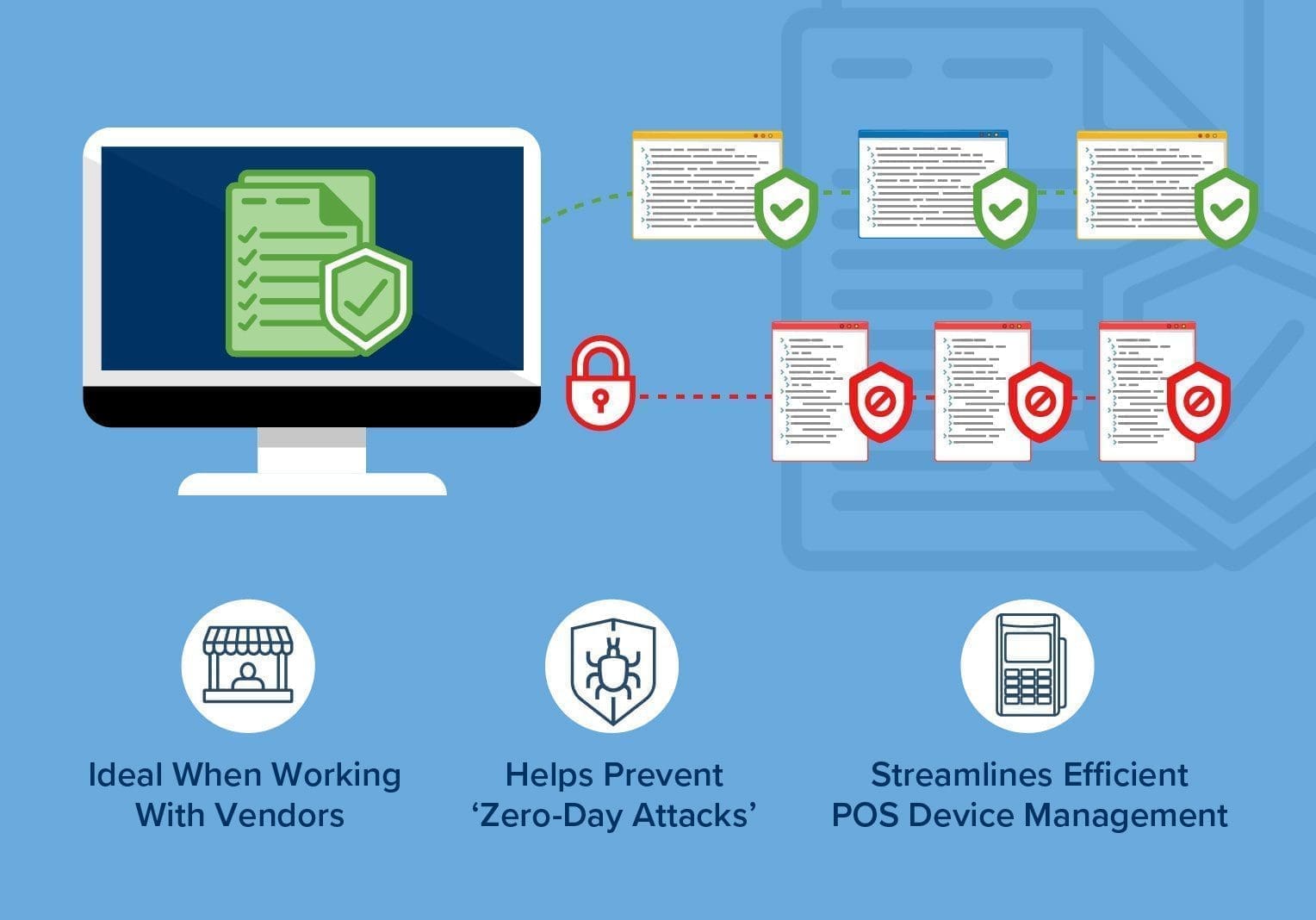
While many attackers are known, POS malware and other cyberthreats are regularly emerging and may not yet be identified. Whitelisting helps to prevent unknown malicious attackers from gaining access to your POS devices and networks. Here a few ways whitelisting can help with protecting your POS system.
- Whitelisting is ideal when working with vendors. Partnering with vendors is a necessity in today’s business environment, but it also presents additional retail cybersecurity threats. It’s difficult to know whether your vendors, particularly those that help manage POS systems, are following the same protocols as your business. With application whitelisting, your business has more control over who can access, when they can access, and the precise places they are allowed to access. It’s a great way to make sure your company practices proper vendor access risk management.
- Whitelisting helps prevent “zero-day attacks.” If there are unknown security flaws in your system or software, zero-day attacks can exploit these and other POS system vulnerabilities. Blacklisting can’t always prevent these attacks, but whitelisting provides heavier regulations that effectively stop zero-day attacks.
- Efficient POS device management. Whitelisting is especially effective for enterprise businesses that manage multiple systems and devices remotely. Secure remote access is vital to avoid time-consuming, expensive fixes, but without proper application whitelisting, remote access solutions aren’t as effective.
Poorly Managed Vendor Access
Trying to manage multiple devices and users, and all their credentials is challenging. If it’s not done effectively, attackers can easily gain access to your devices and network. This is especially true when partnering with vendors who aren’t properly vetted. Attackers can gain access through vendor access points and install malware that skims for sensitive information like credit card numbers and personal data.
When it comes to POS malware attacks, they can happen as a result of insufficient authorization and authentication controls. It’s crucial that IT managers and administrators know that whoever is trying to access their network or devices is who they say are (authentication). Additionally, if they don’t have enough control over what those users have access to, there is potential for unauthorized users to gain access to sensitive information. Often, IT security pros see this as a compromise: follow proper security measures that make things agonizingly slow or move quickly and risk a security breach. Thus, the challenge is how to maintain control while keeping processes efficient.
Take Control of User Authentication and Authorization
With comprehensive remote access tools, IT managers can control authentication and authorization at a granular level. When working with vendors, it’s common to have insufficient credentials for authentication. In fact, some teams let multiple users from the same vendor share access credentials, so they don’t need to create individual user profiles in their directory. Implementing centralized, multi-factor authentication, and integrating with a directory service, can reduce the risk of attackers accessing your network.
With control over authorization, IT staff can manage privileged access by defining which individual users and groups have permission to enter certain parts of your network. Both authentication and authorization are essential to help prevent POS malware attacks. Just because a user is authenticated doesn’t mean they should have access to every part of a network. Authorization does not equal authentication unless that user or group is authorized and authenticated through your remote access protocols.
Retailers Rely on Too Many Security Tools
It may seem like more tools equals more security, but that’s not necessarily true. It can be harder to manage multiple tools leaving gaps in security that make networks more vulnerable to POS malware attacks. Additionally, managing more than one security tool can be more costly and decrease efficiency.
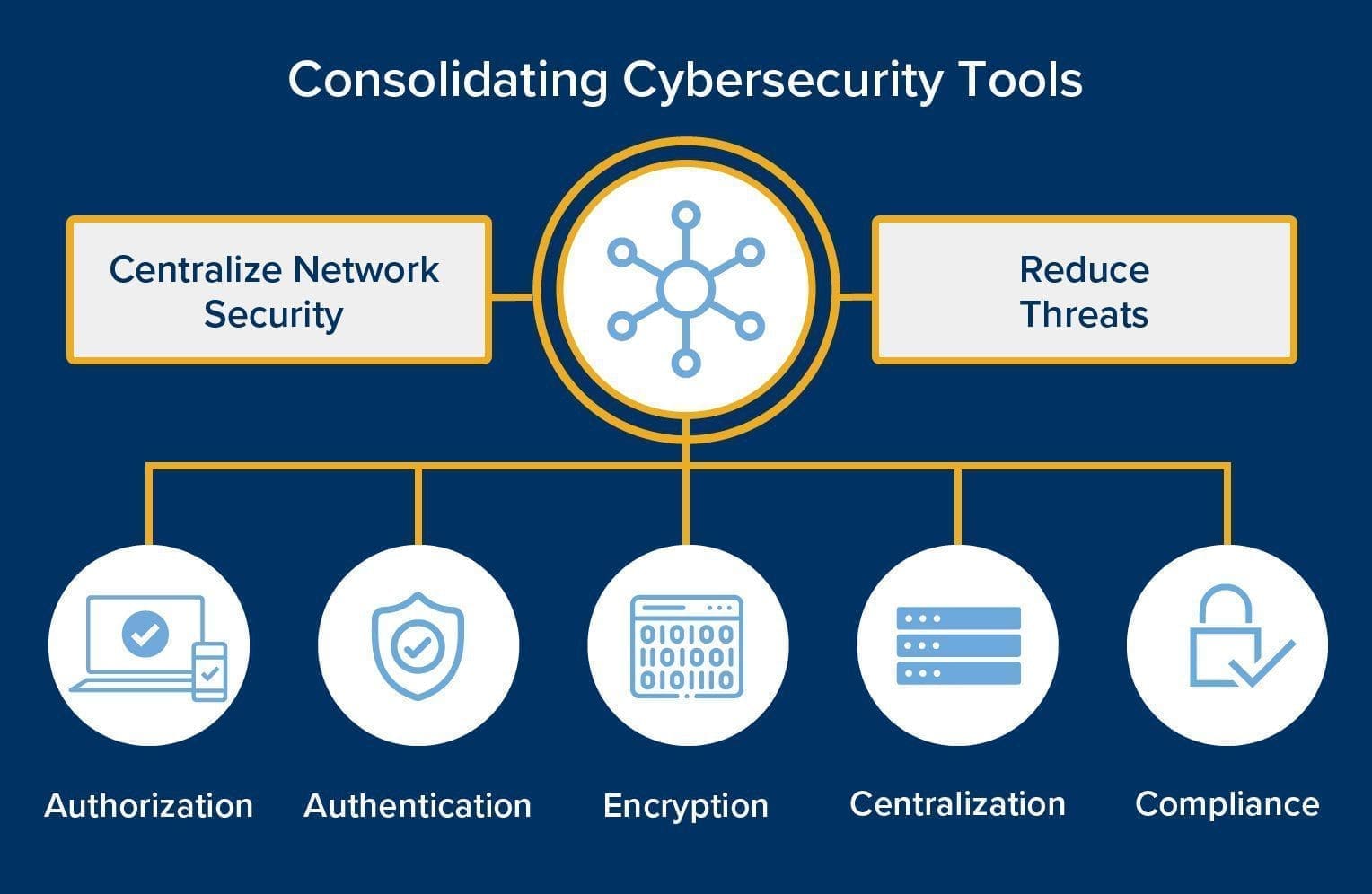
Consolidating cybersecurity tools helps to centralize network security and reduce threats by bringing all the necessary elements into one place: authorization, authentication, encryption, centralization, and compliance.
One of the big problems with retailers is effectively integrating security tools with their operating systems and devices. Cross-platform connectivity is essential to maintain the highest levels of security, but not all software can accommodate multiple operating systems.
Use One Tool to Manage Remote Access
An effective, consolidated remote access tool like Impero Connect, gives retailers secure access to all in-store technology, including digital signage, kiosks, and mobile devices. It also provides cross-platform connectivity with:
- Windows
- Linux,
- Mac OS X
- Toshiba 4690
- Android
With one remote access solution, maintenance is far simpler, helping IT departments manage their time from a single interface, which is important in today’s global environment.
Remote Access Issues and Compliance
Remote access tools are required to follow regulatory guidelines for any country they are operating in. That means there are many guidelines to follow that help with security–but compliance does not always equal comprehensive security.
Standards such as PCI DSS, GDPR, and HIPAA are common. To reduce cyberthreats in the retail industry, PCI DSS is particularly important, as it helps safeguard sensitive financial information.
Yet, many of these compliance standards are simply a good starting point. To truly be effective, remote access solutions need to exceed the basic regulatory guidelines to provide a higher level of service.
Retailers Need Scalable Remote Access Tools
An issue that many businesses face is how to remain compliant and secure as they grow. Depending on the size of your business, you may have to adhere to different guidelines and employ tools that align with your business’ goals.
To successfully grow, your business needs a secure remote access tool that can accommodate your growing business while maintaining the highest compliance standards. With a tool like Impero Connect, you can feel confident that your networks are secure, ready for audits, and capable of expanding along with your business.
Anytime changes are made in IT departments, compliance obligations need to be checked and met. Additionally, it’s important that businesses have audit reports easily accessible. With Impero Connect, you can create custom audit reports with one click so you’re always ready.
Retail cybersecurity is important, but so is securing a network for any business, at any size. Not sure what you need to stay PCI compliant? Download our free PCI Checklist to find out if your remote access tools are working for you and learn about how Impero Connect can help you minimize POS malware and retail cybersecurity threats.



